

Everything You Need to Know About Safe Cryptocurrency Mining
When setting up a GPU rig or ASIC, miners are predominantly focused on how to correctly maximize worker efficiency by optimizing overclocks, energy consumptions and choosing the right coins and pools to mine profitably. But a crucial - and yet often overlooked detail - is securing and ensuring the safety of their equipment.
In this article, we will share steps on how to ensure your farm is kept secured from unauthorized access.
Start with Hiveon OS
Equipment safety needs to be considered in advance. The first step begins with registering a personal account with Hiveon OS.

Specify an active and accessible e-mail address, as you will be required to confirm your account. Next, create your own Hiveon OS login.
Follow these guidelines when creating your password:
- Try to use upper and lower case letters.
- The password needs to have at least one special character.
- The length should be at least 8 characters.
- Avoid reusing passwords from other services.
If you are just starting to get acquainted with Hiveon OS, then this guide will come in handy.
2FA
After registering or logging into your account, we strongly recommend that you enable two-factor authentication in your account settings.
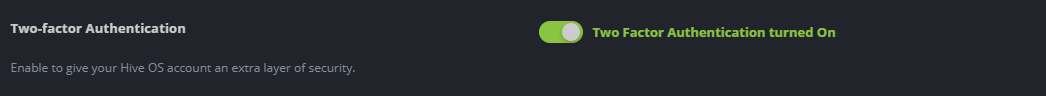
It provides an additional layer of security for your account, ensuring that only you can gain access to your account, even if your password has been compromised.
We recommend that you read the basic safety rules in this article.
VPN
An ISP can see what resources your equipment is accessing over the Internet.
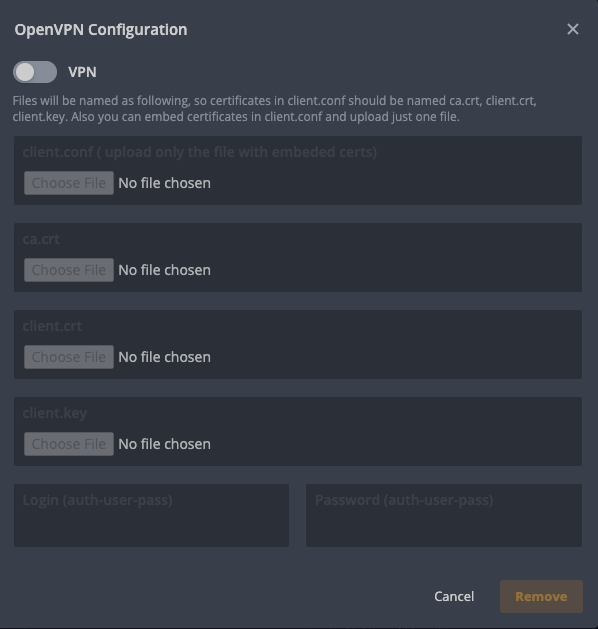
VPN masks your IP address and location securing online connections and bypasses firewalls and geo-blocking among other benefits, but it doesn’t come without possible down sides - VPN can cause slower network speeds, connection throttling, lag and thus increase your stale shares. HiveOn, however, takes this into account by paying 50% of stale shares as long as it’s kept under the overall 5% limit.
This tutorial explains in detail how to set up a VPN connection.
Remote access
The worker can be accessed remotely via multiple ways including SSH, Hive Shell, Shellinabox and Teleconsole.
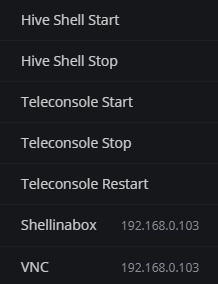
If you want to access a worker that is directly connected to the Internet (ie without a router - for example a direct cable connection from an internet provider, USB GSM modem, etc.) or in a large untrusted internal network (for example, the so-called “Home networks”), you can access it only through ssh (port 22), shellinabox (port 4200), or vnc (port 5900). By default, access is carried out by login (user) and password (1). A password that consists of only one digit is very easy to guess. That is why it is recommended to change the default password. To do this, you can open a hive shell and enter the hive-passwd set YourNewPasswordHere command:
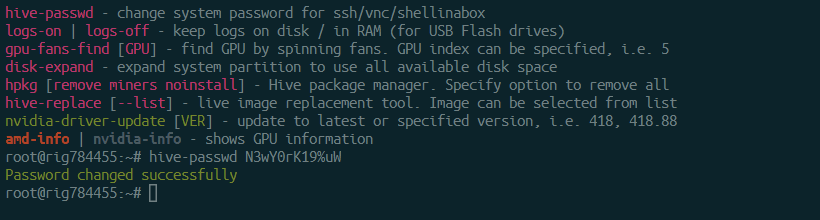
When creating a new password, try following the same guidelines when creating a secure account password.
Port forwarding
In some cases, SSH is open to the internet. It can be closed via port forwarding on your router. It should be noted that these actions can be applied only on a worker with a static ip address. If DHCP is used, then this is not necessary.
DoH
DNS over HTTPS (DoH) is a protocol that enhances user privacy and security by preventing the interception and manipulation of DNS data.
You can enable DoH in the worker settings.
How to prevent phishing?
The best way to protect your account from phishing is to think critically about all information you receive, especially by email or via social media/messaging platforms and channels. Official Hive Team members will never unsolicitedly write to anyone in private.
If you have received a suspicious email you can use these tips to check whether it’s safe:
- Check the email address where it was sent from. Our team and official correspondence can always be recognized by the “@hiveon.net”/”@hiveos.farm” domain names. It’s safe to disregard any others that may or may not look like these, no matter how “official” they may look.
- Try to confirm all your moves through our website instead of clicking any links from the email. If you’re not sure where it comes from, never open any links. No matter how legitimate they may appear.
- Don’t share your passwords or use the same passwords on other sites. Even if it’s for registration in a game - someone might steal your password and try to access your accounts elsewhere.
Email filters generally do a reasonable job at sorting out fake messages and scams, but you still have to be alert when receiving emails. Be especially cautious regarding cryptocurrency payments, as transactions are not reversible in instances where the receiver of the funds is acting under false pretenses.
FAQ
How can I check if my account has been hacked?
In the vast majority of cases, the culprit will have your device mining to a different wallet. Always make sure you check your worker and flightsheets and ensure everything is still set up the way you initially configured it. Your pool dashboard can be a good indicator when checking both historical and current mining activity.
If the flightsheet has a different wallet address, the worker is mining by command line argument without your knowledge, or if the worker appears to be mining on the dashboard, but the pool shows your worker is offline, chances are your worker has possibly been compromised.
What if I am hacked?
- Ensure your network is properly secured against unauthorized external access. Reset and review your router settings and ensure you’re running the latest firmware available for your router.
- Clear all Authentication tokens in your Account Page
- Clear all unknown entries in your farm’s Access tab.
- Reset both your Hive Account (Account Page) and Worker (
hive-passwd YourNewPasswordHere) passwords. - Turn off access via VNC by clearing the first line in
/hive-config/vnc-password.txt. - Turn off 2FA, and turn it on again.
- Make sure to clear any Wallets and/or Flighsheets that you do not recognize as your own.
- Format and reflash your storage device to ensure no compromising scripts or files are left behind.
Conclusion
We at Hive strive to create the best software for miners. Making sure we keep things - especially security - as intuitively and transparent as possible. There are also monitoring bots available in both Telegram and Discord that can be enabled to keep yourself notified of all activities surrounding your farms and workers. By following the steps described in this article, the risk of hacking your account or equipment will be reduced to zero.
🔎 We also have additional security resources available for Hiveon OS: